The “sticky keys” technique for resetting the password on a Windows system is described in many places around the web, but all tend to over-complicate the steps. I’m describing it here for my own reference, so I have a reminder of how it works.
The technique basically provides access to a command prompt from the Windows login page – the page right at the start with an icon for each user. This page appears to run with administrator privileges, so the command prompt can be used to reset any password of any user without knowing any further details.
The command prompt is invoked by moving cmd.exe into the place of the command that handles the “sticky keys” functionality in the login page.
The steps are:
- Rename c:windowssystem32sethc.exe out of the way (to sethc-bak.exe for example).
- Copy c:windowssystem32cmd.exe to c:windowssystem32sethc.exe
- Boot up the PC to the account selection screen.
- Press the shift key five times. This will bring up a command prompt window.
- Reset the password at the command prompt: net user your_user_name new_password
- Log in using the new password.
- Remove c:windowssystem32sethc.exe and restore the saved sethc-bak.exe
The first step involves getting to the file system on the machine. If you just have one machine and Windows 7 install disks handy, then you can boot up the recovery console to a command prompt and rename the files from there.
You may not be able to do step 7 until after a reboot. You may not be able to remove sethd.exe while Windows is running, but you should be able to rename it to sethd-delete.exe or similar to make room to restore the original file.
When I’m recovering the passwords for a laptop, however, I find it easier to just slip the hard drive out and pop it into another machine by USB and rename and copy the files from Windows Explorer. One of these USB-to-SATA docking stations comes in very handy for doing that:

Update
Since posting this, I was given a Windows Vista machine to repair, with which to reset the password. I was unable to rename the files on removing the hard drive and mounting it on my Windows 7 laptop. Windows simply would not let be change anything in the C:Windows folder, complaining about a security issue each time I tried.
In this instance it was necessary to enter the recovery console command prompt, which is pretty much a hidden feature.
To do this, boot from a Windows 7 CDROM then select “Repair Computer”. Once booted, you will be given the option to restore from a previously saved version of Windows. Select that option. Ignore all the errors it gives you about no saved versions being available, but continue until you are able to “Cancel” the process. Once you hit Cancel, you will be presented with this menu:
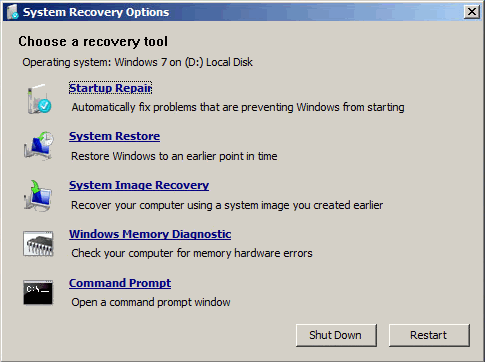
Right at the bottom of the menu is the option to enter the command prompt, and that is where you can rename the system files to turn on the sticky keys hack.

hello jason,
i tried your windows recovery tools methods, but it still asks for the admin password.
what to do?
It could be that Microsoft has “fixed” this loophole for security reasons. It could be that it just doesn’t work any more for other reasons. Or you could be doing it wrong – it is hard to tell. I personally have not had to use this technique for well over a year now, so I don’t know if it does still work (I hope it does).
I would suggest a Google search for “sticky keys” technique to see if other people are finding it no longer works. Any feedback on your findings would be most welcome. Best of luck 🙂
i’m always doing this. and still working! 🙂
The sticky keys technique seems to also work with the latest Windows 10:
http://www.top-password.com/blog/reset-windows-10-password-with-sticky-keys/
I will give it a try when I have time.
Nice find, Vickie.
I found this article offer three ways to help windows password.
https://www.tunesbro.com/reset-windows-10-password.html
This article does market one of the products that the site provides, but there are some other tips in there that you could try first. I don’t endorse the TunesBro products, but the site seem legit.
Update: it seems that this is a product which is being pushed heavily by a lot of affiliates, re-badged under many different names, ALL claiming to have written the software themselves. I don’t know who is behind the core product, but I am always suspicious when the real creators of a security product like this stays hidden behind the scenes. So use with caution – I have no idea what TunesBro, UUkeys, etc. is really installing on your machine.